25 Security Terms You Should Know for Cybersecurity Awareness Month
If you want to reduce your organization’s cyber risk, your employees must take a greater interest in cybersecurity. Brush off your knowledge this Cybersecurity Awareness Month with 25 common security terms.
October is Cybersecurity Awareness Month, and most companies will host at least one workshop, training, or cybersecurity awareness webinar for their employees. Unfortunately, these sessions won’t be very effective if your users don’t understand the most commonly used security terms.
The National Cybersecurity Alliance’s Annual Cybersecurity Attitudes and Behaviors Report found that 53% of participants are always connected online. Some of your employees likely fall into that group. The same study also found that employees mainly believe the IT department (44%) and security department (44%) are responsible for the security of workplace information and that personal responsibility declined by 3%.
Clearly, employers need to take a larger role in ensuring their employees understand the impact of poor cyber hygiene. As Jason Stirland, CTO of The Coaches’ Voice, told Spiceworks in 2022, “Cybersecurity Awareness Month is an ideal time to refresh employees with cybersecurity awareness training. After all, refreshing training ensures employees stay aware of new cybersecurity risks.”
Here are 25 security terms you’ll hear at least once during Cybersecurity Awareness Month. Test your knowledge and be sure you know what they all mean. You never know when you’ll have to explain them to a colleague, client, or relative.
Security Terms – General Threats
1. Advanced Persistent Threat (APT)
An advanced persistent threat (APT) is a form of cyberattack wherein an attacker uses advanced techniques to infiltrate a system or a network and stay undetected for as long as possible. The ultimate goal is to steal critical information over a long period. A lot of effort and resources are required to Since the effort required to carry out such an attack is high, APTs usually aim at high-value targets such as nation-states and large corporations. APT attackers are increasingly going after smaller companies that are part of larger organization’s supply chain networks. Smaller companies don’t have the cyber resources of large organizations and are usually poorly defended, which makes it easier to target them.
Further Reading: What Is an Advanced Persistent Threat? | Everything You Need to Know About Advanced Persistent Threats (APTs) | 6 Tell-Tale Signs of APT Attacks
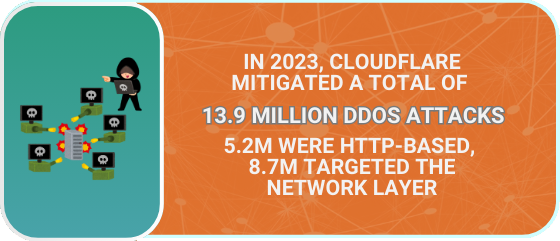
2. Distributed-Denial-of-Service (DDoS)
A distributed denial-of-service (DDoS) attack disrupts a server, website or network by suddenly overwhelming it with large volumes of unexpected traffic it is unable to handle. One common way threat actors use to to carry out a DDoS attack is to first infect thousands of computer systems or IoT devices with malware. These devices are essentially “robots” under control of the threat actor, who uses the combined power of the systems to create a botnet. This botnet is then used to generate large amounts of traffic. DDoS attacks are sometimes also used as a distraction to carry out data theft or network infiltration. According to Imperva’s 2024 DDoS Threat Landscape Report, the number of DDoS attacks year-over-year have increased at dramatic percentages for the gaming (208%), healthcare (236%) and telecommunications and ISP (548%) industries.
Further Reading: What Is DDoS (Distributed Denial of Service)? | How to Stop the Rise of Weaponized IoT Botnets | Botnet Attacks – Examples and Prevention
3. Malware
Malicious software that is purposely developed to damage, disrupt, or infiltrate electronics is referred to as malware. This type of software can also be used when a bad actor wants to open a gateway or backdoors in a system or network. These entrance points allow attackers to remotely plant other malicious software without requiring authentications from the user or system admin. Malware typically stays hidden and causes damage without the knowledge of the user.
Further Reading: What Is Malware? | What Is Malware Removal? | Meet the Top 10 Nastiest Malware of 2020
4. Phishing
Phishing is a widely used term in cybersecurity that describes an attempt to manipulate users into sharing personal or other credentials. These credentials can be used to hijack the victim’s social media or banking accounts. When attackers use emails as the medium for these attacks, they are called phishing email attacks. These emails are deftly crafted so that they look genuine and pique the interest of the target. The objective is to get victims to believe that the email has been sent by a genuine person or an organization to get them to click on the malicious links or attachments and plant malware on their system.
Further Reading: What Is a Phishing Email Attack? | Battling Phishing and Business Email Compromise Attacks | AI Phishing Is Code Red for Businesses
5. Ransomware
Ransomware is a form of malware that uses encryption to block an organization’s access to their systems, files, databases, or applications until they agree to pay a ransom. The software is designed to spread across the network and target database and file servers and can quickly paralyze an entire organization and disrupt business operations. It is considered one of the most lucrative forms of cyberattacks as many organizations choose to pay the ransom to prevent losses incurred due to business disruption. Every year ransomware actors make billions of dollars through ransom payments. To put more pressure on organizations, some ransomware groups also steal critical data before encrypting it and then threaten to sell it on the dark web if the ransom isn’t paid.
Further Reading: What Is a Ransomware Attack? | Ransomware: The Pros and Cons of Paying | The Evolution of Ransomware Tactics

6. Shadow IT
Shadow IT refers to those applications, software, services, or devices that fall outside the purview of an organization’s IT team and have not been vetted and approved for use. Yet, such apps are widely used by business units and users. With the increase in cloud adoption, the use of shadow IT has also grown exponentially to plug the gaps left by company-approved applications. Due to a lack of visibility over shadow IT, IT teams cannot protect them from cyberattacks, putting the entire organization at risk. In 2021, research by 1Password found that more than half of respondents had created multiple accounts the IT department wasn’t aware of, and almost 16% had created more than five accounts.
Further Reading: Mitigating the Risks Posed by Shadow IT | How to Keep Data Safe in the Face of Growing Shadow IT | 7 Factors that Indicate You Have a Shadow IT Problem
7. Spyware
Spyware is also a type of malware but is mostly used for surveillance. Instead of spreading across the network or stealing data, it remains hidden using advanced obfuscation techniques and quietly monitors every activity and communication on the target’s device. Spyware is widely used by criminals to attack high-profile corporate targets. According to a 2023 report from Google’s Threat Analysis Group and Mandiant, commercial surveillance vendors have essentially created a new industry out of selling spyware to take advantage of unpatched zero-day exploits.
Further Reading: What Is Spyware? | Spyware: How to Spot an Infection | What Is a Trojan Horse?
Security Terms – Tactics, Techniques, and Procedures
8. Social Engineering
Social engineering is a set of tactics employed by cybercriminals to gather sensitive information from unsuspecting users. These tactics include background research, social media monitoring, fake customer care calls and sometimes in-person meetings. The motive behind most social engineering tricks is to carry out cyber theft and steal critical information or money. In many instances, attackers use social engineering to target senior-level executives and gain entry into company networks using credentials stolen from them.
Further Reading: What Is Social Engineering?
9. Spear Phishing
A subset of phishing, spear phishing attacks are a lot more sophisticated, organized, and dangerous. Before carrying out these attacks, threat actors use social engineering to identify corporate insiders who may have privileged access to their organization’s critical resources. Bad actors send emails that appear to be from legitimate contacts, like a supply chain partner, a customer, or a coworker. The emails appear relevant to the targeted employee’s work, so the employee is more likely to react to the email by clicking on a malicious link.
Further Reading: What Is a Spear Phishing Attack?

10. Whaling
Also known as CEO fraud, whaling is a more targeted form of spear-phishing attack wherein attackers send a fake email in the name of the CEO or C-level executives to other important officials within the organization. The objective of the attack is to draw the victims to a hoax website and trick them into sharing sensitive information such as their login credentials. This information can then be used to steal money or to launch attacks on company networks.
Further Reading: What Is Whaling?
Security Terms – IT Defense Strategies
11. Biometric Authentication
Biometric authentication is a widely-used method to verify the authenticity of an individual using their biological characteristics such as the face, iris, fingerprint or voice. Most modern-day devices such as smartphones or laptops offer some form of biometric security. With passwords becoming obsolete, enterprises are looking for new ways to secure access to their resources. Biometric security is more secure and reliable than passwords.
Further Reading: What Is Biometric Authentication?
12. Browser Isolation
Most organizations restrict what their employees can access on browsers on their company network or computer systems. This can be frustrating and even throttle productivity in some instances. Browser isolation is a method many organizations use to allow unrestricted web access to their employees without compromising on security. In this method, an employee’s internet activity is isolated from the larger computing environment in which they are operating. This is done by putting all traffic in a sandbox or a virtual machine (local isolation) or by hosting the browsing session on a remote server and streaming it to the user in real-time (remote isolation).
Further Reading: What Is Browser Isolation?
13. Cloud Encryption
With many businesses migrating to the cloud, securing workloads and databases is more critical than ever. Cloud encryption is one of the most effective methods that protect sensitive cloud data from attackers in case of a breach. In this method, mathematical algorithms encrypt all plain text data and transform into ciphertext, rendering it unreadable. Even if an unauthorized user obtains the information, no one can read the content without the decryption keys.
Further Reading: What Is Cloud Encryption?
14. Container Security
Container security is a broad term for a set of tools, policies, and processes designed to make a container more secure and resilient to attacks. With the growing use of containers, attacks on them have also increased. Though they are more secure than traditional virtual machines, they are not impenetrable. According to a Red Hat’s 2024 State of Kubernetes security report nearly 9 in 10 organizations had at least 1 container incident in the previous 12 months.
Further Reading: What Is Container Security?
15. Data Loss Prevention (DLP)
As data volumes grow, managing and keeping track of data has become a lot more challenging. Loss of critical data can have severe repercussions for any organization. It can lead to loss of intellectual property, tarnish the brand image and invite heavy fines from data regulators. Many organizations are turning to data loss prevention (DLP) solutions to improve visibility over their data landscape. DLPs can mitigate the risk of data loss due to insider threats, negligence, external attacks, or natural disasters by ensuring that the organization has consistent access to all its data resources.
Further Reading: What Is Data Loss Prevention (DLP)?
16. Firewall
A firewall is a vital cog in a company’s security architecture. It monitors all incoming and outgoing network traffic as per the IT team’s instructions with the primary goal of allowing non-threatening traffic and keeping out all malicious traffic. A firewall creates a virtual wall between a private network and the public internet. More advanced firewalls come with in-built integrated intrusion prevention systems, enabling them to block malware and prevent application-layer attacks.
Further Reading: What Is a Firewall?
17. Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a key component of any organization’s identity and access management (IAM) strategy. It adds a layer of security over the sign-in process required to access cloud resources, web applications, or a virtual private network (VPN). It requires users to furnish two or more verification factors instead of relying only on the username and password for logging into a system. Studies show that this additional process reduces the risk of a cyber attack considerably. Passwords are the most common type of MFA factor organization use. You can share one-time passwords through email, SMS, or an authenticator tool like Google Authenticator, LastPass, or Okta Verify.
Further Reading: What Is Multi-Factor Authentication?
18. Identity and Access Management (IAM)
Identity and access management (IAM) tools verify the authenticity of requests made by individuals or devices to access systems. IAM solutions improve the IT team’s visibility into who has access to what and ensure that no one misuses access. In the shift to remote work, IAM gained prominence on IT agendas as employees started to request remote access to corporate resources – sometimes with their personal devices.
Further Reading: What Is Identity and Access Management (IAM)?
19. Incident Response
Incident response (IR) is the set of measures an organization takes to minimize the impact of a cyberattack. The measures include detection, analysis, containment, and recovery from a data breach. It also covers post-incident recovery activities such as feeding the information from the data breach to improve the incident response system and provide support to auditors. IR defines the roles and responsibilities of individuals and teams and details communication pathways between the incident response team and the rest of the organization.
Further Reading: What Is Incident Response?
20. Network Access Control (NAC)
Network access control (NAC) is a security solution that keeps unauthorized users and devices from an organization’s private network. As more people use personal devices to access corporate networks, keeping track of who has access to what becomes critical. NAC also makes sense for organizations with large-scale IoT deployments. NAC functions by restricting access to the company’s protected resources to specific users and devices and only to particular areas of the network. So, if a person or device has access to a corporate network, they will still not be able to access any internal resources due to NAC.
Further Reading: What Is Network Access Control?
21. Privileged Access Management (PAM)
A subset of IAM, privileged access management (PAM), is an infosec mechanism that helps organizations manage and secure privileged accounts with access to critical data and accounts. Unlike standard accounts, which have limited access to resources, privileged accounts, if compromised, can have serious repercussions for an organization. Google’s August 2023 Threat Horizons Report found credential issues remain a challenge and account for over 60% of the factors in compromised cloud environments.
Further Reading: What Is Privileged Access Management (PAM)?

22. Password Managers
A password manager is an application that allows users to store and manage their login credentials and passwords. The application stores these credentials in an encrypted database (sometimes called a vault) that nobody can access without the master password. This prevents users from needing to remember multiple passwords: they only have to remember one password to retrieve all others from the vault. Password managers can also generate passwords for users struggling to come up with complex passwords for different accounts on their own. Password hygiene is a big concern for enterprises. According to the 2024 Verizon Data Breach Investigation report, 68% of data breaches included a human element.
Further Reading: What Is Password Management?
23. Penetration Testing
Penetration testing or pen testing is a type of ethical hacking which allows security teams to identify exploitable vulnerabilities in the company’s resources or network by simulating a cyberattack. The objective is to trace the attack paths threat actors use to carry out a cyberattack. This helps in managing associated risks. However, your security team should not run penetration tests during business hours to ensure the test doesn’t impact operations.
Further Reading: What Is Penetration Testing?
24. Threat Modeling
Threat modeling identifies vulnerabilities and improves an application’s security at the earliest development stages. A good threat modeling tool suggests strategies for mitigating vulnerabilities, which developers can incorporate into the application development life cycle. While effective, threat modeling can take time and investment due to scale of your organization and the number of stakeholders involved.
Further Reading: What Is Threat Modeling?
25. Zero Trust Network Access (ZTNA)
Zero trust network access (ZTNA) has emerged as the go-to model for many organizations in the face of rising cyberattacks. The strategy adopts a holistic approach to security, operating on the premise that one cannot trust any individual or device. Zero trust requires organizations to implement strict identity verification for every worker and device trying to access their database on a private network, even if they are located inside the network perimeter. Even if an attacker infiltrates a network, they will not have free access to the resources. Shifting to a zero trust network does not require your organization to invest in new hardware and your IT team can likely implement the strategy using your company’s existing infrastructure.
Further Reading: What Is Zero Trust Security?







