What Is Zero Trust Security? Definition, Model, Framework and Vendors
Zero trust security limits user access in a network, even if the user is already a part of the network perimeter.

Zero trust security is defined as a security model that deems no device, software, or individual trustworthy and instead tests every user and system trying to gain access to any resource in a network. This article looks at the fundamentals of zero trust security, its pros and cons, architectural framework, and the top 10 vendors that can optimize the benefits of zero trust security for enterprises in 2021.
Table of Contents
What Is Zero Trust Security?
Zero trust security is a security model that deems no device, software, or individual trustworthy and instead tests every user and system trying to gain access to any resource in a network.
This concept refers to an IT security approach that keeps sensitive data safe while complying with new privacy regulations. The model validates user identities before giving them direct access to critical IT systems. It utilizes a combination of tools, including multi-factor authentication (MFA), identity and access management (IAM), and endpoint security to authenticate user identities. As a result, unauthorized users are filtered out and prevented from accessing sensitive information.
The zero trust security model can be deployed on diverse networking environments such as cloud, on-premise, and multi-cloud or hybrid setups. It works on the principle of ‘trust nothing, verify everything’. Traditional networks permitted users to access any system, file, or data once they got in. However, in comparison, zero trust segregates different network parts and prevents unauthorized lateral access even if the users get into the network.
Key features of zero trust security
Most zero trust security systems are known to include the following key features:
- Multi-factor authentication (MFA): Multi-factor authentication enables users to use at least two distinct methods to authenticate their identity. The first method involves a normal login with a username and password, while the second one can be a one-time password (OTP) sent to a phone number or email address linked to the account or even security questions.
- Least-privileged access: This feature requires each user to have the lowest level of access to accomplish their task. The method blocks lateral movement and limits damages due to any breach. Additionally, it also avoids misuse of company data by internal company staff.
- Microsegmentation: Microsegmentation refers to a process that divides a network into different zones to allow the entry points to go to one part of the network. This technique limits attacks (if any) to only one section of the network, thereby preventing malware from damaging the entire network.
- Device discovery and identity protection: In a zero trust model, IT administrators need to know the devices operating on the network and the credentials residing on each device. This establishes a benchmark for normal activity on the network. This way, the IT team can easily identify, handle, and red flag any anomalies.
According to a 2021 report by Research and Markets, the global zero trust security market size is predicted to reach a valuation of $59.43 billion by 2028, expanding at a CAGR of 15.2% from 2021 to 2028.
See More: What Is a Security Vulnerability? Definition, Types, and Best Practices for Prevention
Advantages and Disadvantages for Enterprises?
With the rising remote work culture, building a zero trust network has become critical for every organization. However, enterprises need to weigh in on the pros and cons of a zero trust model to decide upon its suitability for their business.
Advantages of zero trust model
Here are the advantages that a zero trust security model comes with.
- Vulnerability management: A zero trust model safeguards a company from in-network lateral threats that could manifest within a network. It makes the network less vulnerable to breaches or attacks.
- Effective user identification policies: The zero trust model uses multi-factor authentication in most cases, but sometimes, the model goes beyond passwords with biometric verification. Such a practice can better guard user accounts. Hence, in zero trust, strong policies are in place for better user identification and access.
- Smart data segregation: A zero trust model lacks a big pool of data that all users access. Instead, data is segmented based on type, need, and sensitivity, making the system more secure. This helps in protecting critical or sensitive data from potential attackers.
- Added data protection facilities: The model protects data that is both in storage and in transit. Additionally, it employs advanced features, including automated backups as a disaster recovery practice, encrypted or hashed message transmission to safeguard moving data, and much more.
- Enhanced security orchestration: A zero trust model ensures that all your security elements work together efficiently and effectively for better security. Inactive security elements are recovered immediately to facilitate 24/7 foolproof protection.
Disadvantages of zero trust model
Although a zero trust model showcases a comprehensive security strategy, it does make security policies complex. Here are some disadvantages of a zero trust model.
- Needs efforts to set up: Introducing new policies on an existing network is challenging, especially during the transition phase. Sometimes, building a new network from scratch is easier than switching over to the same network. Additionally, if legacy systems are not compatible with the zero trust model, starting a new network would be feasible.
- Needs user-specific policies: Managing company employees for access grants is inevitable. However, the user pool extends to clients and third-party vendors as they also use company portals or websites. This implies that, with these add-on access points, a zero trust model needs policies in place specific to each group of users.
- More devices to handle: Today, different users tend to use different devices. Each device has a different set of properties and communication protocols. This means that organizations need to implement and update policies to manage the growing number of devices on the network.
- Complex application management: Likewise, applications are of various types. They are generally used across multiple platforms via a cloud environment. Sometimes, they are also shared with third parties. Hence, a zero trust approach requires better application planning, monitoring, and management depending on users’ needs.
See More: What Is Web Application Security? Definition, Testing, and Best Practices
Zero Trust Security Model and Framework
Zero trust has become crucial for organizations as the digital frontier is impacting their business network security architecture. A zero trust security model provides a complete security suite for an organization. Enterprises can leverage greater granular control over accessibility, better visibility, and improved analytics and automation to keep the policies in check and update them as and when needed.
Zero trust model
A zero trust model has seven main components — zero trust data, zero trust networks, zero trust people, zero trust workloads, zero trust devices, visibility and analytics, and automation orchestration. Let’s understand each one in detail.
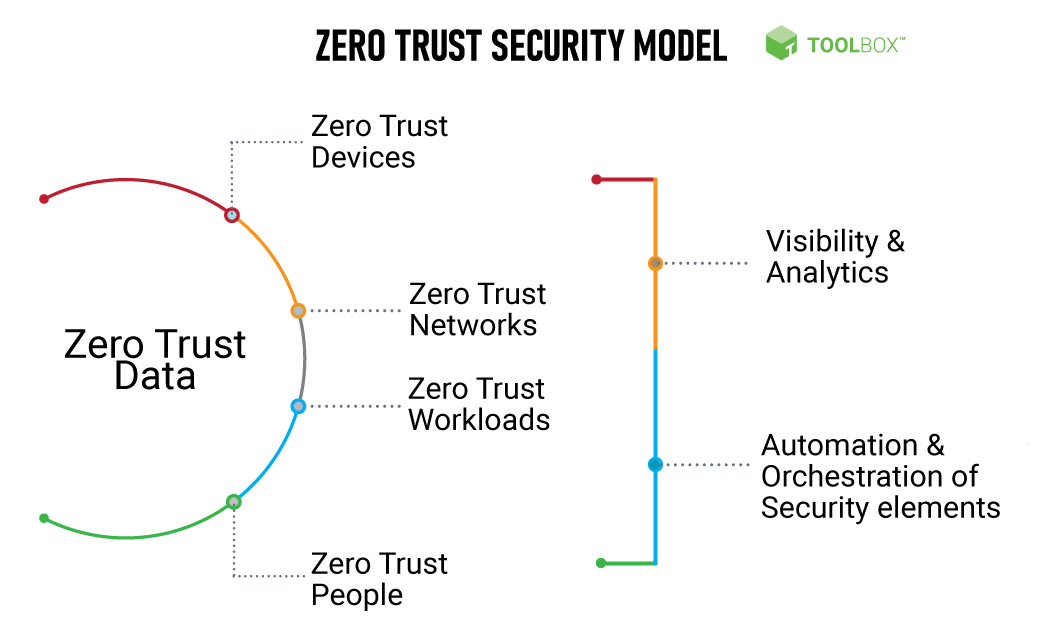
Zero Trust Security Model
- Zero trust data: Data protection is a priority in the zero trust model, followed by supplementary protection layers. If a cybercriminal breaches the network perimeter, exploits vulnerabilities, or illicitly collaborates with an insider, they would have less accessibility to critical data. Also, policies will be in place to respond to the attack immediately before it becomes a formal breach.
Data is the primary target of most attackers and insider threats, and it is considered a vital pillar of a zero trust model. Data protection can happen when organizations understand who has access to it, whether the data is sensitive or stale, and whether an attack response is in place to manage potential threats. - Zero trust networks: For attackers to steal your data, they must be able to navigate across the length and breadth of your network. However, a zero trust model makes this challenging as it segments, isolates, limits, and restricts the network with advanced next-gen firewalls.
- Zero trust people: In a security strategy, humans represent the weakest pillar. Hence, in zero trust, all users—inside the network and on the internet—are monitored to track how they access resources and verify their activity. Also, users are monitored to prevent inevitable mistakes of falling prey to phishing, bad passwords, or suspicious insiders.
- Zero trust workloads: Enterprises have several applications and software components that allow customers to interact with them. Any unpatched customer-facing application, API, or software can act as an attack vector. Zero trust regards the entire system, right from storage, operating system, to web front-end, as a threat vector. It further deploys zero trust-compliant controls for better protection against such vectors.
- Zero trust devices: With the advent of IoT and the high demand for smart devices worldwide, device count has grown exponentially in the past few years. Here, each connected device can act as an entry point for attackers to infiltrate your network. With a zero trust security approach, security teams are better positioned to manage and control every device on the network.
- Visibility and analytics: With zero trust principles, organizations have better visibility of everything happening over their networks. Methods such as advanced threat detection and user behavior analytics can help identify suspicious behavior in real-time.
- Automation and orchestration: Zero trust security enables automation that can help in disaster recovery and keeps systems up and running. Automation in a zero trust model aids in faster remediation and advanced threat detection. It also saves human resources as automation tools can perform incident response, thereby focusing on other important tasks at hand.
Architectural framework
The National Institute of Standards and Technology (NIST) observes that zero trust implementation requires an architectural framework with definite logical components. This framework controls access to resources, and monitors data flow transitioning into and within the network.
In August 2020, NIST released a publication titled ‘NIST Special Publication 800-207: Zero Trust Architecture’, which details the logical components of a typical zero trust architecture, design scenarios, and threats. The publication also establishes zero trust principles for enterprises wishing to leap zero trust security.
Here are the fundamental elements of the zero trust framework as defined in NIST SP 800-207.
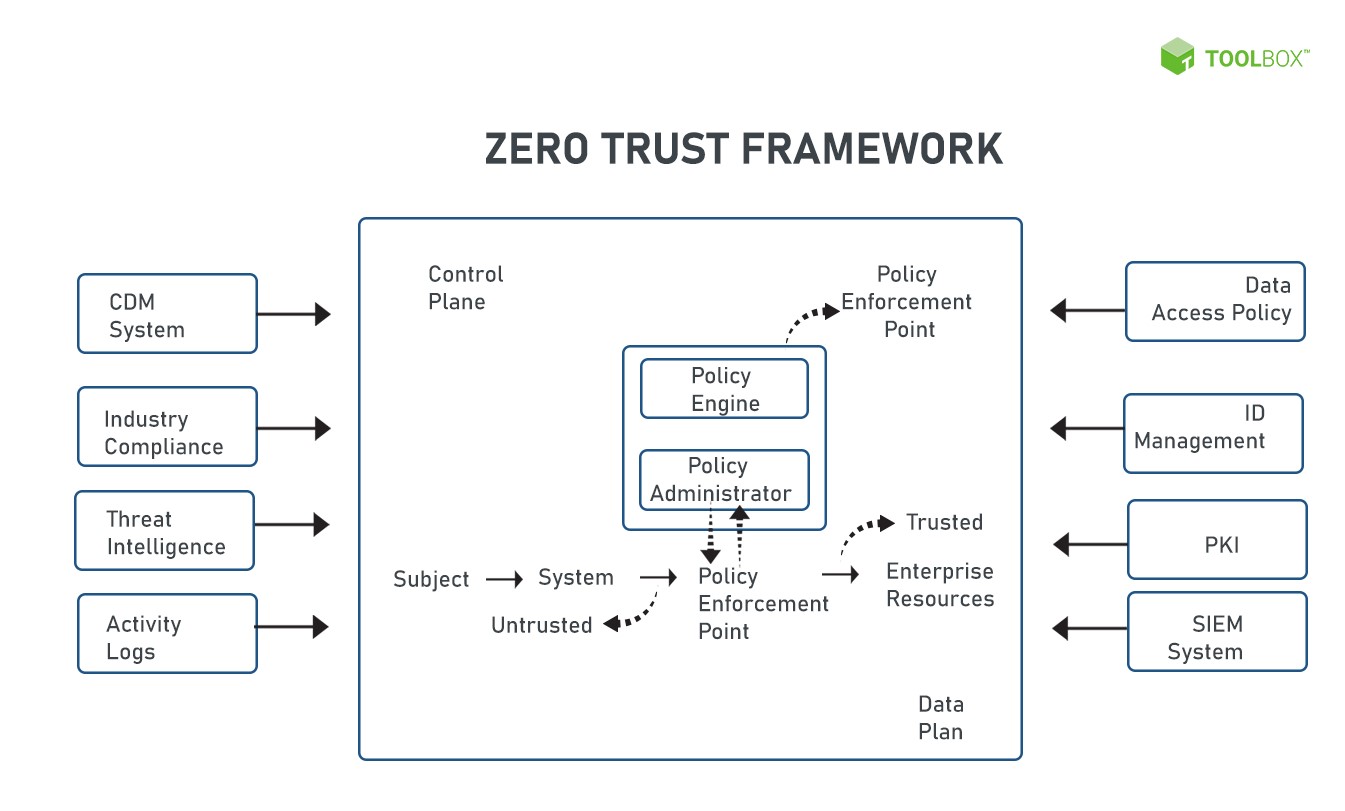
1. Policy engine: The policy engine decides whether to grant access to a resource or deny for a subject. It uses policies by the enterprise and outside sources such as continuous diagnostics and mitigation (CDM) systems and threat intelligence services to grant, deny, or revoke access to target resources. This policy engine is also coupled with a policy administrator.
2. Policy administrator: The policy administrator links or delinks the communication path between a subject and a resource. It is responsible for generating client credentials or authentication tokens used by the client to access a resource. It takes help from the policy engine to continue or discontinue a session. The public administrator establishes a communication path with the help of policy enforcement points via the control plane.
3. Policy enforcement point: The policy enforcement point acts as an intermediary between a subject and an enterprise resource as it enables/disables communication between them. The component can be further divided into a client (user) and resource side (gateway). Beyond the enforcement point, enterprise resources are hosted in a trust zone.
4. Data access policies: This component details the rules and policies for gaining access to enterprise resources. These policies can either be encoded or generated on the go by the policy engine. Authorization of resources begins with these very data access policies. Additionally, these rules define the primary access privileges for accounts and applications in an enterprise.
5. Identity management system: This module creates, stores, and manages the accounts and identity credentials of users in an enterprise. Necessary user details such as name and email ID are present within the system, along with organizational attributes such as user role and access privileges. The zero trust system often considers public key infrastructure (PKI) to deal with artifacts linked to user accounts.
6. Security information and event management (SIEM): SIEM gathers security-related data for future analysis. The collected data is then used to update policies and create awareness over potential attacks against the enterprise.
7. Threat intelligence: This module communicates information from various sources that allow policy engines to make informed access decisions. The information can relate to new vulnerabilities that can threaten the enterprise in the future. Additionally, the component also blacklists newly detected malware and reported attacks. Inputs from this component are then relayed to the policy engine to grant or deny access to an enterprise’s assets.
8. Network and system activity logs: This component collates asset logs, network traffic logs, resource access events, and other aspects that reveal the security position of an enterprise’s IT system in real-time.
See More: Top 10 Threat Modeling Tools in 2021
Top 10 Zero Trust Security Vendors in 2021
This section lists the top 10 zero trust vendors with good user ratings and provides a comprehensive security strategy to an enterprise’s network.
1. Akamai
Overview: Akamai is a popular zero trust vendor that provides a cloud-based model. Its zero trust model incorporates dynamic and transparent policies for enhanced security.
Product: Akamai Intelligent Edge
Features:
- Akamai’s product offers a single sign-on (SSO) with MFA
- Safeguards against distributed denial-of-service (DDoS) attacks, thereby allowing secure data processing with a smooth workflow
- Offers identity-based security
- Enables advanced threat protection
- Assists in inline data inspection
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Akamai’s products (e.g., Intelligent Edge) are compatible with most APIs. They provide a user-friendly interface for easy monitoring and threat management. However, some users have reported issues such as data vulnerability risks as the product stores data on a third-party cloud. Additionally, default rules exercised by the product can sometimes block valid user requests.
2. Cisco
Overview: Cisco offers a zero trust solution that secures access across the entire enterprise’s environment. It protects everything, right from applications to folders.
Product: Cisco Zero Trust
Features:
- Cisco’s product (Zero Trust) provides policy-based control over the network
- Gives detailed logs, reports, and alerts
- Provides greater visibility with an eye on any form of access across your network
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Cisco’s Zero Trust is suitable for companies having remote task forces as it provides a consistent security experience for all employees, be it remote or in-office staff. However, some users have reported that the product requires hands-on management from the IT team. Additionally, the implementation and deployment of the product is a time-intensive process.
3. Cloudflare
Overview: Cloudflare’s zero trust solution provides a steady login experience to every user, device, and application in a network.
Product: Cloudflare Access
Features:
- Provides easy remote access from any location
- Enables micro-segmentation
- Seamless integration with open source software and social identity providers
Pricing: Cloudflare access is a part of Cloudflare teams, free for up to 50 users. Following rates apply as per team:
- Teams Free – $0/user
- Teams Standard – $7/user
- Teams Enterprise – Custom
Editorial comments: Cloudflare Access is suitable for compliance-friendly organizations as the product obeys compliance rules by accessing logs in real-time via an interface. It enforces the default deny rule by working with identity providers and endpoint protection platforms. However, some users have reported issues that this default deny rule can sometimes block valid requests.
4. Illumio
Overview: Illumio offers a comprehensive, end-to-end zero trust security model by eliminating any insider or outsider. It provides microsegmentation and allows data isolation and data encryption, and easy data control for securing valuable data.
Product: Illumio Core
Features:
- Illumio Core offers microperimeter security
- Provides complete protection for data in transit
- Enables end-to-end security for data
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Illumino Core gives reliable traffic discovery and visualization features. It also provides good customer and engineering support. However, some users have reported issues with the reporting feature. Users have to apply filters time and again to get what they want in a report.
5. Palo Alto Networks
Overview: Palo Alto Networks is a top IT security provider with zero trust security offerings that are a part of its network security suite.
Product: Palo Alto Networks (Zero Trust Solution)
Features:
- The product offers advanced integration with other security elements
- Provides granular visibility as the product has a central console for viewing network happenings.
- Offers multi-factor authentication features
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Palo Alto Networks provides detailed reports along with threat responses. It also has responsive technical support. However, some users have reported frequent updates as the product is still in the developing stage. A few users also say that the product often requires several months for implementation.
6.Symantec
Overview: Symantec provides a cyber-defense platform to enable a zero trust model. The solution manages encrypted data traffic and also uses behavioral analytics to identify threats.
Product: Symantec’s Zero Trust Solution
Features:
- Utilizes a strong web application firewall
- Provides a user control and authentication toolkit
- Harnesses security analytics for better future preparedness
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Symantec’s Zero Trust Solution is suitable for organizations opting for a remote work module as the solution effectively manages secure remote workforce access. This, in turn, reduces the VPN overhead. However, some users have reported issues related to the vulnerability of application firewalls as new malware, and sophisticated algorithms could trick such security products.
7. Okta
Overview: Okta offers a popular zero trust solution that is easy to set up and implement. It also helps users stay compliant with various international standards.
Product: Okta Identity Cloud
Features:
- The product is centered on identity access management (IAM) and zero trust policies
- Offers multi-factor authentication (MFA)
- Provides single sign-on (SSO) feature
- Automates process-driven workflow, e.g., employee onboarding and offboarding process
Pricing: Okta Identity Cloud provides multiple packages depending on product features. Standard rates include the following:
- $2.00 per user per month – Single Sign-on
- $3.00 per user per month – Multifactor Authentication
- $5.00 per user per month – Single Sign-on Adaptive
- $6.00 per user per month – Multifactor Authentication Adaptive
Editorial comments: Okta Identity Cloud is suitable for enterprises handling a large pool of international users as the product stays compliant with several international security standards. However, some users have reported issues related to the initial setup, which can turn out to be quite complex. Also, first-line support sometimes faces hurdles when dealing with complicated problems.
8. Forcepoint
Overview: Forcepoint provides a wholesome zero trust solution that is suitable for managing a safe remote workforce.
Product: Forcepoint Private Access
Features:
- Forcepoint ‘s product is a next-generation firewall
- Offers continuous network monitoring
- Employs data loss prevention strategy
- Implements network protection and micro-segmentation
- Offer data traffic decryption for full visibility and instant threat inspection
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Forcepoint’s product is suitable for remote workers as it eliminates any complexities and risks of VPNs since it gives them access to required applications. However, some users have reported issues highlighting organizations’ vulnerability as data is stored on third-party clouds.
9. Unisys
Overview: Unisys offers a complete zero trust implementation with a five-step mechanism: prioritize, protect, predict, isolate, and remediate.
Product: Unisys Stealth
Features:
- Stealth product offers micro-segmentation and full visibility
- It offers cloud and mobile support services
- Provides an intuitive and customizable interface
Pricing: Pricing details are only available upon request on the company website.
Editorial comments: Unisys Stealth implements a comprehensive five-step methodology that helps in faster risk mitigation. However, some users have reported issues that the product lacks on-premise deployment options for Mac devices specifically. Also, the product does not perform well with network traffic analysis.
10. AppGate
Overview: AppGate offers risk-based solutions that provide customizable rules for authentication and threat prevention.
Product: AppGate SDP
Features:
- Reduces attack surface
Verifies user identity based on user role, date, time, location, etc.
Blocks lateral movement and offers micro-segmentation - Pricing: Pricing details are only available upon request on the company website.
Editorial comments: AppGate SDP is suitable for organizations targeting isolated environments and requiring granular access control across multi-cloud frameworks. The product also has responsive user support. However, some users have reported issues related to the management interface as it is quite complicated to operate.
Let’s compare the features of these solutions again:
| Solution/ Feature | Multi-factor authentication (MFA) | Least-privileged access | Microsegmentation | Device discovery and identity protection |
|---|---|---|---|---|
| Akamai | Excellent | Yes | Yes, but limited | Yes |
| Cisco | Yes | Excellent | Excellent | Yes |
| Cloudflare | Excellent | Yes | Yes | Yes |
| Illumio | Excellent | Yes | Yes, but limited | Yes |
| Palo Alto Networks | Yes | Excellent | Yes | Yes |
| Symantec | Yes | Excellent | Yes, but limited | Yes |
| Okta | Yes | Excellent | Yes | Yes |
| Forcepoint | Yes | Excellent | Yes | Yes |
| Unisys | Yes | Yes | Yes, but limited | Yes |
| AppGate | Yes | Yes | Yes, but limited | Yes |
See More: What Is Password Management? Definition, Components and Best Practices
Takeaway
A zero trust model is based on the ‘never trust, always verify’ principle. It keeps a check on access to resources, files, folders, and systems within a network. The model makes remote access, IoT, and cloud environments more reliable, secure, and trustworthy. Hence, businesses must embrace such a security solution to overcome ever-evolving cyber threats.
Do you think zero trust security completely shields an enterprise’s network? Comment below or let us know on LinkedIn, Twitter, or Facebook. We’d love to hear from you!






