What Is a Phishing Email Attack? Definition, Identification, and Prevention Best Practices
Phishing email attacks are designed to draw potential targets into divulging sensitive information such as account credentials or download malware.

A phishing email attack is defined as a form of phishing wherein attackers use authentic-looking emails that prompt targets to perform a certain action. These actions might result in loss of sensitive data, malware downloads, or even financial loss. This article introduces you to the basics of a phishing email attack and identifying one and shares some best practices for prevention in 2021.
Table of Contents
- What Is a Phishing Email Attack?
- 5 Best Ways to Identify a Phishing Email
- 7 Best Practices to Prevent Phishing Email Attacks in 2021
What Is a Phishing Email Attack?
A phishing email attack is a form of phishing wherein attackers use authentic-looking emails that prompt targets to perform a certain action. These actions might result in loss of sensitive data, malware downloads, or even financial loss.
Phishing is the act of defrauding victims by posing as a trustworthy entity and exploiting human vulnerabilities to gain sensitive information. This may be personal information such as social security numbers or even critical information that helps gain access to the organization that the target is working for. Phishing can be done through text messages, voice calls, emails, or even by tweaking search engine results.
The first known email phishing attack was recorded in the mid-1990s when hackers tricked AOL users into revealing their user credentials. The word ‘phishing’ is a play on fishing for information combined with phone-based phreaking attacks that were carried out to trick telecom providers into giving free phone calls. With the increase in sophistication of technology and most of the world moving online, successful phishing attacks have become one of the easiest yet most damaging types of cyberattacks.
Most prevalent types of phishing attacks
-
- Email phishing: These are phishing attacks that operate primarily through emails. Attackers usually create a generic yet authentic-sounding email and send it out to a large pool of targets.
- Spear phishing: Spear phishing is a more specialized form of email phishing where hackers research a specific target and make the fraudulent email as personalized as possible. It is more successful than bulk email phishing and tends to have more severe consequences.
- Vishing and smishing: Vishing is phishing for information through phone calls. Smishing is using text messages: SMSes and instant messages to do the same.
- Whaling: Whaling is a form of spear phishing where the potential victim is usually a high-profile individual within a target organization. Compromising high-ranking executives may result in leaking proprietary organizational information or administrative credentials that can be used to control parts of the company’s infrastructure.
- Angler phishing: Angler phishing is when hackers scour through social media looking for consumer complaints and then pose as customer relations managers to gather more information.
This article focuses on email phishing attacks. The main difference between phishing email attacks and spear phishing attacks is the number of targets. Most cyberattacks use phishing as phase 1, using emails to gain access into enterprise systems.
The goal of all phishing attacks is one of two things:
-
- Extract information: When a phishing email aims to get some sort of information from the target, it usually uses genuine-looking websites to trick users into entering the required information. One of the most common forms of a phishing email is the sender pretending to be from a bank or financial institution. Hackers trick bank customers into thinking that the bank’s systems have been compromised and need to change their account credentials. The customer is then directed to a phony bank page, where scripts are run to store this information.
- Infect the target system: These types of phishing emails aim at making the victim install malware or spyware on their own systems. This is usually done by using attachments that need to be downloaded. For example, the COVID-19 pandemic created an uptick of spoofed email messages with attachments outlining necessary medical and personal precautions.
Also Read: What Is Whaling Phishing? Definition, Identification and Prevention
Why organizations need to be wary about phishing email attacks
According to the 2019 Verizon Data Breach Investigations Report, almost one-third of all data breaches in 2018 and 2019 involved phishing. 94% of the malware was found to be delivered by email. So what makes phishing emails so effective? Phishing attacks fall under the spectrum of technology-driven social engineering. Social engineering is defined as the manipulation of basic psychology to get people to perform certain actions, usually resulting in them divulging confidential information. It leverages the fact that people are inherently trusting, believing that no one is out to scam them. The phishing email attack itself is not tech-focused but using tech instead as a vehicle to gain access.
The effectiveness of phishing email attacks can also be attributed to the ease of execution. The Dark Web offers several off-the-rack phishing kits and templates that hackers simply have to deploy in their copycat websites. Phishing kits are bundles of website resources and deployment tools that are used to host spoofed websites. This means that minimal technical skills are enough to pull off an email attack. In most cases, this website is usually a login page with malicious scripts. Once this fake website is in place, hackers simply send out a blast of emails urging potential victims to visit and engage with this website.
As we have seen so far, phishing email attacks depend on two things: important assets that are stored and handled online and manipulation of human instinct. The onset of the COVID-19 pandemic in 2020 saw most of the world move online. Enterprises allowed their employees to work remotely, accessing crucial resources from outside the company network. This unprecedented situation meant that most communication happened via email, and the use of file-sharing applications significantly increased. It also meant that business protocols and processes had to be revised, redrafted, and communicated. Hackers clearly saw this as an opportunity.
Barracuda Sentinel announced that in March 2020, it detected 467,825 coronavirus-related phishing emails as opposed to just 1,188 emails in the month preceding it. According to Kroll, ransomware incidents increased in 2020: 26% of them were delivered by email. Uncertainty of the pandemic caused more people to react without their usual safety fallbacks in place. In fact, Verizon found that users are three times more likely to click on pandemic-related phishing scams than non-COVID-related ones.
Almost all government agencies across the world released statements warning their citizens about this increase in the number of phishing email attacks. This is why organizations need to start building a robust anti-phishing system within their security landscape. Even without a global crisis, phishing email attacks have proven to cause huge revenue and reputational losses.
Also Read: What Is Phishing? Definition, Types, and Prevention Best Practices
Real-world examples of phishing email attacks
1. Wire fraud that stole $100 million from big tech companies
A scammer posed himself as a third-party vendor and sent phishing invoice emails to employees of Facebook and Google, among others. He was successful in extracting around $100 million dollars between 2013 and 2015 until he was finally noticed and caught. In this case, he specifically targeted employees who had permission to conduct multi-million dollar transactions to pay for these invoices. Targets were the organizations themselves, and the loss was financial.
2. 2013 Target breach
For around 20 days surrounding Thanksgiving 2013, Target was subject to the second-largest credit, and debit card data breach in the U.S. Forty million debit and credit card numbers were stolen, along with seventy million personal information records. The cause of this breach was traced back to an email phishing attack, not at Target, but at a third-party vendor that connected to Target’s system. Target notified the data breach to the U.S. Justice Department, triggering a thorough investigation. Customers filed class-action lawsuits, alleging negligent behavior by the retail giant in not protecting customer data. Target paid out $18.5 million in settlement to these customers. The CEO and CIO of the vendor company were fired for not having proper security protocols in place. In this case, the victims were customers, and the organizations’ losses were reputational and financial.
3. Celebrity nude leaks of 2014
In 2014, a hacker sent phishing emails to celebrities and A-listers that appeared to be from Google and Apple. These emails warned the targets of compromised accounts and urged them to change their credentials. This allowed the attacker to gain access to email inboxes and subsequently other accounts such as iCloud. It resulted in the leakage of hundreds of sensitive photos of numerous celebrities. These examples prove that no matter how sophisticated an organization’s system is, it is only as strong as the people controlling the system. This does not mean that these specific people were easily duped. It just means that the emails were painstakingly made to look and sound authentic to both humans and content filtering systems.
Also Read: What Is a Spear Phishing Attack Definition, Process, and Prevention Best Practices
5 Best Ways to Identify a Phishing Email
Before we get into the best ways to identify a phishing email, let’s have a look at the three key aspects of every email-based phishing attack:
1. Setting up shop: This involves setting up trustworthy servers and finding legitimate IP addresses to use. IP addresses may be in the same range as those of the company that the hackers are pretending to represent. They may also build the reputation of IP addresses by first sending legitimate emails. A valid IP address is key to being let into the target network by its security controls.
2. Sense of urgency in the communication: Phishers usually try to evoke one of two emotions from their targets: fear or sympathy.
-
- Fear: This is done by threatening the loss of data or services if an action isn’t taken. For example, an email saying that the payment to your supplier has not gone through and your shipment may not arrive, or if you do not renew the subscription, you may lose the data stored there forever.
- Sympathy: This is done by creating an alarming scenario to evoke the target’s sympathy. For example, emails that appear to be received from the National Center for Missing and Exploited Children or emails from WHO asking for bitcoin donations to deal with the COVID pandemic.
3. Call-to-action: The tone of the email urges the victim to perform an action — usually clicking on a URL or downloading an attachment. This step leads to the actual theft of information or infection of target assets.
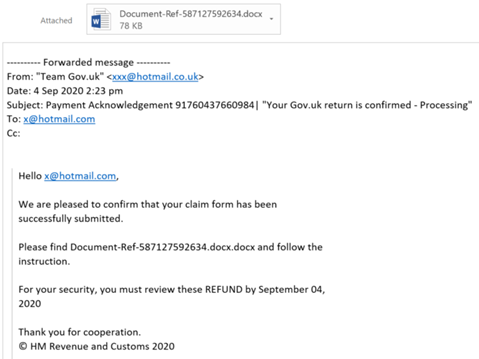
Phishing Email Example
Source: GOV.UK
Also Read: Whaling vs. Spear Phishing: Key Differences and Similarities
5 ways to identify a phishing email
1. Email structure and content
If an email appears with urgent messaging and asks you to do something out of the ordinary, it is best to have it confirmed with the appropriate department or people involved. For example, if one receives an email about compromised online accounts, the bank can be contacted to verify if it is true. It’s important to note that most large organizations do not ask for sensitive information, especially via email.
2. The sender and email ID
The biggest clue of the authenticity of the email is the sender. All valid email addresses usually have the organization’s name in the email address. For example, an email about a PayPal account from ‘[email protected]’ is probably a scam. A Paypal employee’s email ID would usually be something like ‘[email protected]’. Phishers also try to make the sender’s email address look similar, if not the same, as valid email addresses. In this Paypal example, they might try to use ‘[email protected]’. They may also substitute alphabets with similar-looking characters or symbols to fool victims. For example, using ‘paypaI’ as the domain with a capital ‘I’ instead of lowercase ‘L’.
3. The language used One of the telltale signs of a phishing email is the use of generic language. Most companies address their customers by name, as opposed to ‘Dear valued customer’. This is a red flag. Another red flag is if there is no salutation at all and the email directly starts with the content.
Corporate emails are also devoid of spelling and grammar errors. Some of these errors are because the hackers may not be native English language speakers. Some are also done on purpose to allow these emails to pass through content filters.
Spam emails may also not have the same tone of communication as original emails from the organization they’re posing to be from. For example, it is easy to spot a change in the tone of an email from a supplier who has been doing business with the target for a long time.
4. Attachments in the email Most companies do not send unprompted emails with attachments in them. Most hacker email attachments have .exe, .zip, or .src extensions. These extensions are most likely to install the malware in the target’s device and are best avoided. Most legit organizations sharing important documents do so from their websites and usually have an authentication mechanism in place.
5. URL and hyperlinks Most phishing emails have a hyperlink that the victim has to click on to access information instead of spelling it out in the body of the email itself. This usually leads to a website that looks valid, but on closer inspection, may not follow the UX design of the actual company’s website. Another giveaway is the URL itself. Like the sender’s email domain, this is also spoofed to look almost the same as the original, but it can never be the same. Look for the same kind of flags as with the email domain: changed characters, odd numbers appearing at the end of it, etc. It is good practice to manually go to the company’s website and log in to check the validity of the communication instead of clicking directly on email links.
HMRC’s example email above checks each of these flags, except the suspicious URL. Phishing emails tend to use only one mode of attack at a time: attachments or URLs.
The most common type of phishing emails appear to be from:
-
- The government: This includes federal government agencies, insurance-related intimations, healthcare notifications, etc. Phishers also pose as executives from the tax department, sending communication about tax refunds, etc.
- Suppliers and vendors: These are companies that do daily business with the organization. Such phishing emails generally talk about failed payments, delayed services, etc. This information can be easily lifted from the target company’s website or social media accounts.
- Friends and colleagues: Social media has made tracking of friends and colleagues very easy for hackers, who exploit this information to send more personal-looking emails to unsuspecting victims.
- Security administrators: In large enterprises, security administrators send regular emails reminding employees of password rotation and intimating them of the latest malware. Some phishing emails leverage this trust to send fake emails such as ‘this is a security audit, we require you to verify your account’.
- Financial institutions: Phishing emails posing to be from banks are the most common ones. This means direct access to the employee’s or organization’s finances.
Also Read: Spear Phishing vs. Phishing: Key Differences and Similarities
7 Best Practices to Prevent Phishing Email Attacks in 2021
Phishing email attacks can be prevented by following certain practices personally or within an organization. Here are the top seven practices that can lead to more protection from phishing.
Best Practices to Prevent Phishing Email Attacks
1. Conduct regular employee training
Even with security controls in place, employees are the last line of defense for any organization. The success of a phishing email attack ultimately rests on people who receive these emails. This is why regular employee training is essential. Information such as identifying phishing emails must be revised at regular intervals to keep employees on their toes. Employees should also have regular briefings on good password hygiene, especially rotating account passwords.
2. Run phishing simulations
Phishing simulator tools are available in the market to mock typical phishing attacks. These simulators carry out actual phishing campaigns triggered internally by the security team. Phishing simulations reduce an organization’s social engineering attack surface. Phishing simulations are usually part of employee training. They allow companies to spot vulnerabilities in business policies, communication plans, infrastructure, and assets.
3. Have appropriate security controls in place
As stated before, phishing email attacks involve the exploitation of both human and technical vulnerabilities. This means that employee training must happen in tandem with the implementation of appropriate security controls. Security tools that are required to fight phishing attacks include:
a) Phishing simulation tools, as noted above.
b) Content filtering solutions scan all content going in and out of the company’s network to check for suspicious activity. It involves checking payload structure and flagging content that falls in denylists. Content filtering solutions also restrict access to certain categories of content from within the company’s network. The two important filtering subsets required to spot phishing emails are email gateways to spot spam emails and website filters to prevent damage from malicious URL clicks.
c) While email filters block suspicious-looking emails right at the gate, post-delivery protection services are designed to secure emails already within the company network. They use machine learning algorithms and threat intelligence to scan and identify emails for potential threats.
d) Antivirus and anti-malware solutions.
Another form of validating important emails is using digital signature certificates to authenticate the sender. These certificates make it impossible for hackers to mimic high-level employees. These tools are the first line of defense against phishing. For true protection, companies must have multiple layers of security. For example, if a phishing email does manage to elude these tools, an IAM or PAM system must be in place to prevent access to critical resources.
Also Read: Top 10 Anti-Phishing Software in 2021
4. Implement business protocols for high-stake actions
While creating business policies, organizations must make it a habit to involve security personnel to spot security holes. All high-risk or high-stake operations must have a documented business process that employees need to follow and complete. For example, payment processes must involve different people with multiple levels of authorization. The more the number of people involved, the less likely they are to fall prey to a phishing scam. Another example is getting unexpected vendor payment requests approved by higher executives.
5. Use multi-factor authentication
Phishing email scams run on the assumption that just gaining account credentials can allow them access to crucial data and assets. This can be addressed by implementing multi-factor authentication (MFA), especially for accounts that access crucial operations. MFA authentication uses more than just the traditional username and password for user authentication. It involves an additional level of authentication, such as sending a time-bound OTP to the employee’s mobile phone.
While hackers may gain access to user credentials, they will not be able to gain access to the account itself because of such additional and independent steps needed for authentication.
6. Establish a communication plan when suspicious emails are discovered
Companies must have a proper communication plan in place for when employees come across phishing emails. The plan needs to establish who the employees need to intimate in case of a successful attack or how to flag unsuccessful attempts to warn other employees. Such an escalation is important to stop the spread of a phishing attack.
Organizations can also look into implementing a human firewall system. A human firewall is a group of committed employees who prevent suspicious activity by reporting them. They consciously follow best security practices. The more the number of employees committed to being part of this firewall, the more effective this concept becomes.
7. Verify emails through other channels
Manual intervention is an effective way to thwart phishing email attacks. This involves using a second mode of communication to verify the contents of an email. For example, if a partner firm asks for sensitive information, call its office to confirm. If a supplier emails with an issue, contact the supplier directly to resolve the issue.
Takeaway
Emails have become a ubiquitous part of everyday operations. This leads people to believe that emails are safe and often harmless from a security standpoint. However, most adults don’t even understand what phishing is. Even with state-of-the-art security controls in place, employees need to be made aware of various types of phishing and trained on identifying them. This combination of tech and human controls gives complete 360-degree protection against cyberattacks.
Did this article help you understand phishing and how you can best prevent it? Tell us on LinkedIn, Twitter, or Facebook. We would love to hear from you!






