Top 10 Endpoint Detection and Response Tools in 2022
Endpoint detection and response (EDR) tools continuously monitor endpoint devices in enterprise networks to detect signs of compromise and initiate remediation.
Endpoint detection and response (EDR) tools continuously monitor endpoint devices in your network to detect signs of compromise and initiate remediation. EDR technology will boom by 2028, providing enterprises with options at every price point and use case requirement. This article discusses the top 10 solutions in this category, along with the five essential features to look for.
Table of Contents
Top 5 Key Must-Have Features of EDR Tools in 2022
Endpoint detection and response (EDR) is defined as a cybersecurity solution that constantly monitors endpoint devices such as laptops, mobile phones, workstations, and virtualized desktops, along with endpoint users, to detect signs of a cyberattack and resolve them either through automated remediation or by alerting a human stakeholder.
Key Features of EDR Tools
An endpoint detection and response tool has two main components – a data collection and processing engine and a remediation module. Whenever a threat actor (external or insider threat) tries to breach an endpoint, it will result in suspicious device activity. The endpoint devices could be showing abnormal memory usage, users could appear to log in at unusual times, or the system may run slower than usual. The tool monitors devices 24/7 to collect data and check for these signals.
Once the data collection and processing engine has picked up a signal, it will be assigned a risk score, triggering an alert. An IT administrator or cybersecurity analyst can view the alert (along with contextual information) to investigate the threat and resolve it manually. Or, simple anomalies can be resolved or blocked through automation. Alert mechanisms and automated threat remediation rules are housed in the remediation module.
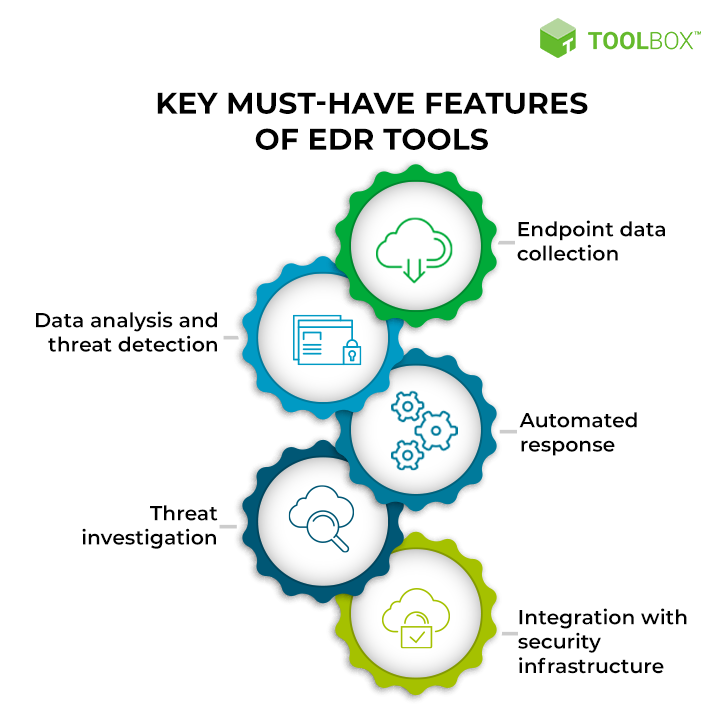
Endpoint detection and response is central to IT security, particularly in the remote working era. According to Dark Reading’s State of Endpoint Security 2021 Survey,84% of cybersecurity professionals believe that all attacks start at an endpoint. 70% are looking to protect against this through increased end-user training, and more than one in three plan on increasing their investments in EDR tools. If you are looking to deploy the best EDR tool for your organization, here are the five features to look for:
1. Endpoint data collection
Endpoint data collection is a foundational capability for every EDR tool. Typically, the solution helps you install an agent on every endpoint device. The agent monitors the device 24/7, collects data, and conveys it to a centralized hub for processing. The agent should also not be very resource-intensive. Otherwise, it will consume too much memory and computing power and slow down device performance.
2. Data analysis and threat detection
The EDR tool should analyze the data collected by endpoint agents to generate threat insights. Advanced solutions use artificial intelligence (AI), machine learning (ML), and even deep learning to correlate data from multiple endpoint devices to provide users with contextualized insights. Tools may include a threat database and white-listed traffic to benchmark suspicious activity.
3. Automated response
Once a threat is detected, the tool should initiate a response workflow, starting with prioritized alerts. Alerts should ideally have a risk score so that IT managers and security analysts know which ones to prioritize. Simple or obvious threats should be automatically blocked by the EDR tool, with the details properly recorded in the event logs. You may also opt for tools that offer automation guidance and playbooks for users.
4. Threat investigation
Threat investigation capabilities allow users to understand a threat before deciding how to remediate it. The EDR tool must generate contextualized information on threats to assist in the investigation process and find the threat’s root cause. Some tools also offer threat pathway visualization features that let users understand how the threat passed and impacted endpoint systems.
5. Integration with security infrastructure
The endpoint detection and response tool you choose should work alongside the other technologies in your security stack. The vendor may provide additional security solutions, which can be natively integrated with minimal effort. Or, the vendor may partner with other industry providers to offer out-of-the-box solution connectors. Some tools have an open architecture, which is highly flexible.
See More: What Is a Security Vulnerability? Definition, Types, and Best Practices for Prevention
Top 10 EDR Tools in 2022
From $1.9 billion in 2020, endpoint detection and response solutions are expected to be worth $11.22 billion by 2028, according to a report by Reports and Data published in November 2021. That’s more than a 10x increase in less than a decade, giving organizations several powerful EDR options to choose from. Here’s our roundup of the top 10 EDR tools for 2022, arranged in alphabetical order.
Disclaimer: This list is based on publicly available information and may include vendor websites that sell to mid-to-large enterprises. Readers are advised to conduct their final research to ensure the best fit for their unique organizational needs.
1. Bitdefender Endpoint Detection and Response (EDR)
Overview: Bitdefender is a Romanian cybersecurity company founded in 2001. It offers several endpoint protection products, from antivirus to container security to EDR.
Key features: The key features of Bitdefender Endpoint Detection and Response (EDR) include:
- Endpoint data collection: It monitors your network and endpoint device landscape to detect suspicious activity early on.
- Data analysis and threat detection: It has powerful EDR analytics capabilities and correlates data across multiple endpoints, aided by contextualized data from the XDR module.
- Automated response: It streamlines response through data visualization and automatic sandboxing of suspicious files, with the option to delete, blacklist, kill or isolate threats.
- Threat investigation: Its cloud-based event collector helps investigate threats across your infrastructure and includes threat intelligence.
- Integration with security infrastructure: It can integrate with third-party security software and supports connected workflows.
USP: Bitdefender has a cross-endpoint correlation engine that collects and distills endpoint events to prioritize threats and create multi-level views of security incidents. This speeds up threat investigations significantly.
Pricing: Bitdefender EDR is a custom-priced solution built on Bitdefender GravityZone, starting at $110.99.
Editorial comments: Bitdefender is a comprehensive EDR solution that offers protection against zero-day threats. However, administrators require careful configuration, which can be effort-intensive.
2. Cisco Advanced Malware Protection (AMP) for Endpoints
Overview: Cisco is among the world’s leading network, security, and communications systems providers. Cisco AMP (also called Cisco Cisco Secure Endpoint) provides end-to-end protection for endpoint devices.
Key features: The key features of Cisco AMP include:
- Endpoint data collection: It collects data from the entire endpoint environment, using Orbital Advanced Search to connect with every device.
- Data analysis and threat detection: It uses behavioral analytics, machine learning (ML), and signature-based techniques to analyze data and find threats.
- Automated response: It offers automated playbooks to define and execute threat responses.
- Threat investigation: It has a built-in threat hunting module based on the MITRE ATT&CK framework of adversary tactics and techniques.
- Integration with security infrastructure: It natively integrates with Cisco’s vast suite of security solutions and third-party tools.
USP: Cisco AMP offers an advanced malware analysis feature right out of the box. Using the product’s Secure Malware Analytics Cloud module, you can conduct a forensics breakdown of a cyberattack.
Pricing: Pricing for Cisco AMP starts at $55.99 for one node.
Editorial comments: It is a reliable solution and lets users gain from ML. However, the solution can be resource-intensive. Some users have also reported occasional false positives.
3. Cortex XDR
Overview: Cortex XDR is an endpoint detection and response tool by cybersecurity company Palo Alto Networks.
Key features: The key features of Cortex XDR include:
- Endpoint data collection: It provides complete visibility into network traffic and user behavior by scanning 100% of connected endpoints.
- Data analysis and threat detection: It leverages cloud-based analysis, artificial intelligence, ML, and patented behavioral analytics to detect threats.
- Automated response: It automatically visualizes the pathway and context for every attack and groups them for faster response.
- Threat investigation: Users can investigate the root cause of any alert with a single click and gain from the company’s WildFire threat intelligence database.
- Integration with security infrastructure: It integrates with other tools in your security operations center (SOC) through application programming interfaces (APIs).
USP: It has a sophisticated deep forensics feature for internal and regulatory endpoint investigations. Importantly, it lets you conduct forensic analysis even if the endpoint is not connected to the network.
Pricing: Pricing for Cortex XDR starts at approximately $90 per endpoint.
Editorial comments: Cortex is a powerful EDR tool with a command-line interface (CLI) and AI and ML capabilities. However, customers have reported false positives due to dynamic updates and delayed support.
4. Cynet 360
Overview: Cynet is an Israel-based cybersecurity company founded in 2015. It offers a unified platform for endpoint protection, spanning antivirus, EDR, ransomware protection, and other key capabilities.
Key features: The key features of Cynet 360 include:
- Endpoint data collection: It discovers and connects with all the endpoints in your enterprise perimeter to provide visibility into device, network, and user behavior.
- Data analysis and threat detection: It offers advanced endpoint detection techniques to detect both known and unknown threats.
- Automated response: It can automatically trigger a response with a high-risk alert based on pre-built workflows.
- Threat investigation: You can investigate threats by analyzing lateral movement and deploying decoy files to lure attackers.
- Integration with security infrastructure: You can integrate Cynet 360 with external tools through the company’s managed services.
USP: Cynet 360 streamlines endpoint incident response through a pre-built remediation toolset. This includes file, host, network, and user entities, custom scripts, and automated response playbooks.
Pricing: Pricing for Cynet 360 is undisclosed.
Editorial comments: Cynet includes 30+ threat intelligence feeds to qualify endpoint data. However, it requires a significant amount of training to use the user interface (UI) and complex dashboards.
5. FortiEDR
Overview: FortiEDR is an endpoint detection and response tool by American cybersecurity company, Fortinet. The company offers network, cloud, endpoint, and zero-trust security products.
Key features: The key features of FortiEDR include:
- Endpoint data collection: It connects with all endpoints (including legacy operating systems and manufacturing systems) and collects data for proactive vulnerability assessment.
- Data analysis and threat detection: Its risk mitigation-based policies help correlate data and immediately detect vulnerabilities.
- Automated response: Its ML-based antivirus prevents infection from file-based malware and stops breaches with real-time post-infection blocking.
- Threat investigation: It continuously gathers evidence on potential threats and enriches the data to aid in investigations through a guided interface.
- Integration with security infrastructure: The tool’s Fortinet Security Fabric architecture makes it easy to integrate with other solutions like FortiGate, FortiNAC, FortiSandbox, and FortiSIEM.
USP: Customers can opt for the company’s FortiEDR Deployment Services. This makes it simpler to design the architecture, plan configurations, install FortiEDR, set up playbooks, and finetune the environment.
Pricing: Pricing for Cynet 360 starts at $29 per endpoint.
Editorial comments: The solution is comprehensive and provides several value-adding features like guided interfaces and patented code-tracing technology. However, users have noted that the licensing model can be confusing without enough clarity into the features included.
6. Huntress
Overview: Huntress is a U.S.-based cybersecurity company founded in 2015. It provides easy-to-use endpoint protection solutions for managed service providers and IT teams.
Key features: The key features of Huntress include:
- Endpoint data collection: Its lightweight agent collects comprehensive data from endpoints to detect attacks.
- Data analysis and threat detection: The EDR tool identifies suspicious activity and the company’s threat hunters review the activity to generate incident reports.
- Automated response: You can respond to incidents by isolating endpoints, one-click attack blocking, or manual threat remediation.
- Threat investigation: It provides detailed summaries and branded reports to aid in threat investigation.
- Integration with security infrastructure: It offers an API library for integrations and supports custom integrations.
USP: The tool includes a host of value-added services like early ransomware detection, managed antivirus, external reconnaissance, and more. This reduces efforts for teams with complex security needs.
Pricing: Pricing is undisclosed, but you can gain from a free trial.
Editorial comments: Huntress is a lightweight yet powerful EDR tool. However, keep in mind that it does not integrate with security information and event management systems (SIEM) as its reports are in a different format.
7. SanerNow
Overview: SanerNow is an endpoint detection and response tool by the Indian cybersecurity company, SecPod. SecPod offers enterprise solutions for endpoint, asset, and patch management, with a special focus on compliance.
Key features: The key features of SanerNow include:
- Endpoint data collection: It uses multiple lightweight agents to monitor endpoints and collect data in real-time.
- Data analysis and threat detection: It analyzes data for issues, risks, and threats, which are visualized on a central console.
- Automated response: It supports automated workflows to streamline end-to-end tasks and threat remediation.
- Threat investigation: It detects deviations and anomalies in real-time and lets you investigate through natural language search queries.
- Integration with security infrastructure: It has a flexible architecture with RESTful APIs, enabling a wide range of integrations.
USP: SanerNow combines EDR with patch management and compliance management. You can automate cross-platform patching and define policies for PCI, HIPAA, NIST 800-53, and NIST 800-171.
Pricing: Pricing for SanerNow is undisclosed.
Editorial comments: SanerNow is ideal for teams looking to manage endpoint security and overall risk using one solution. However, the dashboards don’t offer customization. Plus, the admin reporting features can be improved according to users.
8. SentinelOne
Overview: SentinelOne is a U.S.-based cybersecurity company founded in 2013. It is known for its sophisticated autonomous AI capability, which powers the SentinelOne ActiveEDR solution.
Key features: The key features of SentinelOne include:
- Endpoint data collection: It scans endpoints 24/7 to collect data and all incident-related events.
- Data analysis and threat detection: It analyzes the data and maps incident pathways using its patented Storyline technology for actionable correlation.
- Automated response: It includes a patented one-click remediation feature that helps remediate an attack automatically and roll back file versions to an uncorrupted state.
- Threat investigation: It provides cybersecurity analysts with helpful indicators and attack technique context for streamlined investigations.
- Integration with security infrastructure: It integrates with the external security orchestration, automation, and response (SOAR) workflows so that telemetry data can flow across systems.
USP: This EDR tool has a cloud-hosted Binary Vault where you can store suspicious files and malicious executables for up to 365 days. This allows analysts to investigate the threat and discover new insights over time.
Pricing: Pricing starts at $6 per agent per month with additional fees for data storage beyond 14 days.
Editorial comments: SentinelOne EDR is useful for deep investigations into endpoint threats. However, users have noted issues with scalability and remote upgrades.
9. Sophos Intercept X
Overview: Sophos is a U.K.-based security software and hardware company founded in 1985. Sophos Intercept X is the company’s 360-degree solution for endpoint protection, powered by deep learning technology.
Key features: The key features of Sophos Intercept X include:
- Endpoint data collection: It collects data from multiple endpoints and incorporates cross-device data sources for unified visibility.
- Data analysis and threat detection: Its AI and deep learning algorithms enable signatureless data analysis to detect known and unknown threats.
- Automated response: It enables automated exploit prevention by blocking attackers, assisted by its managed threat response team.
- Threat investigation: You can investigate the root cause of threats, export forensic data, and benefit from SophosLabs Threat Intelligence.
- Integration with security infrastructure: The tool can be integrated with other Sophos solutions. Plus, the company offers a developer platform to manage APIs.
USP: The tool has a unique Active Adversary Mitigation feature that lets you detect the presence of benign threats, even if they do not cause anomalies. This helps you preempt attacks before they can happen.
Pricing: Intercept X endpoint protection pricing starts at $28 per node.
Editorial comments: Sophos’ deep learning makes it an accurate and effective EDR tool. However, support can be delayed depending on your region, which is an issue noted by several customers.
10. VMware Carbon Black EDR
Overview: VMware is a U.S.-based computing technology company founded in 1998. Its EDR solution results from its acquisition of the endpoint security leader Carbon Black in 2019.
Key features: The key features of VMware Carbon Black EDR include:
- Endpoint data collection: It collects and visualizes comprehensive data on endpoint events and matches the information against automated watchlists.
- Data analysis and threat detection: It analyzes data and enables intuitive attack chain visualization to provide insights into the attacker’s behavior.
- Automated response: It supports automated and remote response so that users can pull or push files, kill processes, and perform memory dumps.
- Threat investigation: It provides users with cloud-delivered threat intelligence to aid in investigations and proactive threat hunting.
- Integration with security infrastructure: It has a robust partner ecosystem and open platform architecture to simplify integration with your existing security stack.
USP: In addition to endpoint protection, VMware offers optional detection and response features for your containerized and cloud-based workloads. This drives comprehensive security using one solution.
Pricing: Pricing for VMware Carbon Black starts at $38.40 per node.
Editorial comments: VMware carbon Black EDR offers excellent protection without being intrusive. However, customers have noted that there is a lack of technical support and the tool can be resource-intensive during boot-up.
See More: What Is Privileged Access Management (PAM)? Definition, Components and Best Practices
Product Comparison of the Best EDR Tools in 2022
Here are the key highlights of the best EDR tools in 2022:
| Product | Features | Pricing | Verdict |
|---|---|---|---|
| Bitdefender Endpoint Detection and Response (EDR) | Its cross-endpoint correlation engine collects and distills endpoint events to prioritize threats and create multi-level views | Bitdefender EDR is a custom-priced solution built on Bitdefender GravityZone, which starts at $110.99. | It protects against zero-day threats. However, it requires careful configuration, which can be effort-intensive. |
| Cisco Advanced Malware Protection (AMP) for Endpoints | Its out-of-the-box malware analysis feature lets you conduct a forensics breakdown of a cyberattack. | Pricing for Cisco AMP starts at $55.99 for one node. | It is a reliable solution and lets users gain from ML. However, it can be resource-intensive and occasionally generates false positives. |
| Cortex XDR | Its deep forensics feature lets you conduct analysis even if the endpoint is not connected to the network. | Pricing for Cortex XDR starts at approximately $90 per endpoint. | Cortex is a powerful EDR tool with CLI, AI, and ML. However, there may be false positives due to dynamic updates, and support can be delayed. |
| Cynet 360 | It streamlines incident response through a pre-built remediation toolset for file, host, network, and user entities. | Pricing for Cynet 360 is undisclosed. | Cynet includes 30+ threat intelligence feeds to qualify endpoint data. However, it requires a significant amount of training to use the UI and dashboards. |
| FortiEDR | The company’s FortiEDR Deployment Services helps in architecture design, configurations, installation, and playbook setup. | Pricing for Cynet 360 starts at $29 per endpoint. | It provides several value-adding features. However, the licensing model can be confusing without enough clarity into the features included. |
| Huntress | It includes a host of value-added services like early ransomware detection, managed antivirus, external reconnaissance, and more. | Pricing is undisclosed, but you can gain from a free trial. | Huntress is a lightweight yet powerful EDR tool. However, it does not integrate with SIEM as its reports are in a different format. |
| SanerNow | It combines EDR with patch management and compliance management for PCI, HIPAA, NIST 800-53, and NIST 800-171. | Pricing for SanerNow is undisclosed. | SanerNow helps manage endpoint security and overall risk using one solution. However, the dashboards are not very customizable, and admin reporting features can be improved. |
| SentinelOne | It has a cloud-hosted Binary Vault where you can store suspicious files and malicious executables for up to 365 days. | Pricing starts at $6 per agent per month with additional fees for data storage beyond 14 days. | SentinelOne EDR is useful for deep threats investigations. However, customers have noted issues with scalability and remote upgrades. |
| Sophos Intercept X | Its Active Adversary Mitigation feature lets you detect the presence of benign threats, even if they do not cause anomalies. | Pricing for Intercept X endpoint protection starts at $28 per node. | Sophos’ deep learning makes it an effective EDR tool. But support can be delayed depending on the region. |
| VMware Carbon Black EDR | It offers optional detection and response features for your containerized and cloud-based workloads. | Pricing for VMware Carbon Black starts at $38.40 per node. | It offers excellent protection without being intrusive. However, there is minimal technical support and the tool is resource-intensive during boot-up. |
Key takeaways
Endpoint detection and response tools help protect one of the most important threat vectors in the enterprise, i.e., endpoint devices and users. Here are the key takeaways to keep in mind when selecting the best-fit EDR tool for your organization:
- EDR is a billion-dollar market with options available for every price point and use case.
- Look for key features like device protection, email security, cloud-based control, sandboxing, and security awareness training when evaluating the tools available to you.
- Prioritize AI and ML for analysis and automated remediation. These features can significantly reduce cybersecurity effort and errors.
As you grow your endpoint landscape to support hybrid work and employee flexibility, EDR tools keep your organizations safe from insider and external threats.
What features are you looking for in EDR as the reliance on remote endpoints grows? Tell us on LinkedIn, Twitter, or Facebook. We’d love to hear from you!
MORE ON ENDPOINT SECURITY
- What Is Endpoint Encryption? Definition, Architecture and Best Practices
- Top 10 Endpoint Security Vendors in 2021
- What Is Endpoint Security? Definition, Key Components, and Best Practices
- What Is Extended Detection and Response (XDR)? Definition, Components, Advantages, and Best Practices
- How Enterprises Can Secure Endpoints With Extended and Managed Detection and Response





