Secure Your Endpoints with Extended and Managed Detection and Response
The proliferation of endpoint devices, coupled with the scale of remote work, has complicated endpoint security. Organizations can streamline endpoint management through an extended detection and response (XDR) approach. Managed detection and response (MDR), which outsources XDR to a third-party vendor, can shift the burden off of your internal staff.
Most organizations focus on endpoint detection and response (EDR) because user devices and servers are the most common attack targets. However, this is not enough today. That’s why many organizations are moving from EDR to an extended detection and response (XDR) approach. This ensures your organization of any size can continuously look at all resources to detect anomalous behavior. Quick detection of many attacks requires looking at all activity across all information resources, including the cloud. Doing this 24/7 is the most effective approach. Still, the volume of resources may make it impractical for in-house deployment, which is where managed detection and response (MDR) comes in.
Limitations of Relying Only on EDR
Many experts believe that EDR is reactive. It detects threat actors on endpoints by matching known signatures and attack patterns using threat intelligence, machine learning, and advanced file analysis.
EDR is often part of an overall endpoint protection platform (EPP) solution. Paul Webber describes EPP as prevention and detection tools that:
- Prevent and protect against threat actors
- Analyze device and user behavior
- Investigate incidents and provide remediation guidance
- Collect and report on systems inventory and system configurations
- Manage and report on firewall and encryption
- Scan for vulnerabilities
- Provide threat intelligence
Because EDR focuses on endpoints, it may not detect issues that stem from connected devices or network traffic. It also isn’t designed to monitor cloud behavior. Additional tools are needed to expand detection and response efforts into other areas not usually included in EDR. Further, multiple solutions are often used for EDR, making managing detection, response, and security a decentralized effort. Decentralization often prevents the effective aggregation and correlation across all solutions. Extended detection and response is the answer to this challenge.
Improve Visibility and Detection with Extended Detection and Response
XDR provides a broad look via a single portal of what is happening across the enterprise, including cloud services. The top solutions integrate out-of-the-box with various security solutions. Gartner defines XDR as “a SaaS-based, vendor-specific, security threat detection and response tool that natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.”
XDR removes the requirement for having to monitor multiple solutions individually. It also enables aggregation of all relevant information to analyze endpoint, network, and cloud behavior. Further, XDR is supported by machine learning and analysis across detection, investigation, and response tools.
Figure 1 (below) shows how Symantec describes an extended detection and response solution. It is essentially the common model across all solutions that enables human threat management supported by AI and machine learning. It uses data stores to analyze current and historic behavior across all information resources and networks.
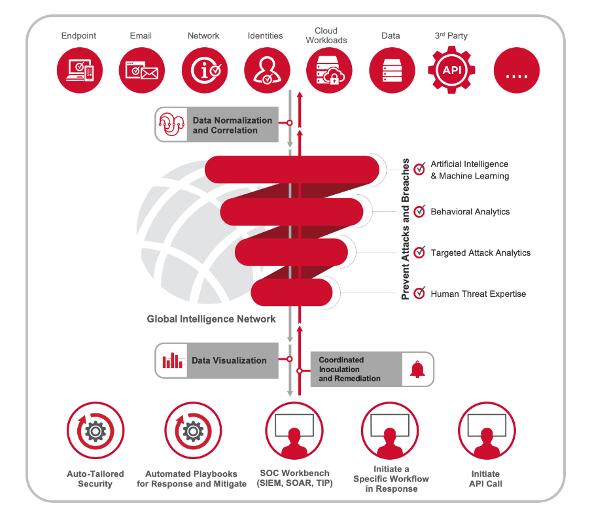
Figure 1: Symantec XDR
XDR is a good approach, but it still requires human interaction for alert assessments and initial response. Again, this is best done 24/7 by a dedicated team. For most organizations, this requires MDR.
Managed Detection and Response: Additional Resources for XDR
MDR is not a technical solution. It is an approach to how an organization manages XDR or other approaches to detection and response activities. It relies on a third party to detect, identify, triage, and respond to potential security incidents.
Gartner describes an MDR provider as an entity that remotely manages incident detection and response, including
- Detection, investigation, and response capabilities across all technologies
- Providing staffing with the skills needed for threat monitoring and detection; and incident response
- Documented workflows and procedures that fit the customer organization’s operating environment
- The assumption that the SOC should not just wait for IoCs; threat hunting is part of the service
- Use of tools, techniques, and procedures that support XDR on customer premises and in the cloud
- Taking responsibility for determining what and how threats are detected.
Figure 2 (below) shows the phases in one of the incident response methods, as defined in NIST SP 800-61, Computer Security Incident Handling Guide. An organization must detect, analyze, contain, eradicate, and recover business functionality quickly to reduce business impact. An effective response requires a trained team with security, network engineering, server engineering, and other expertise.
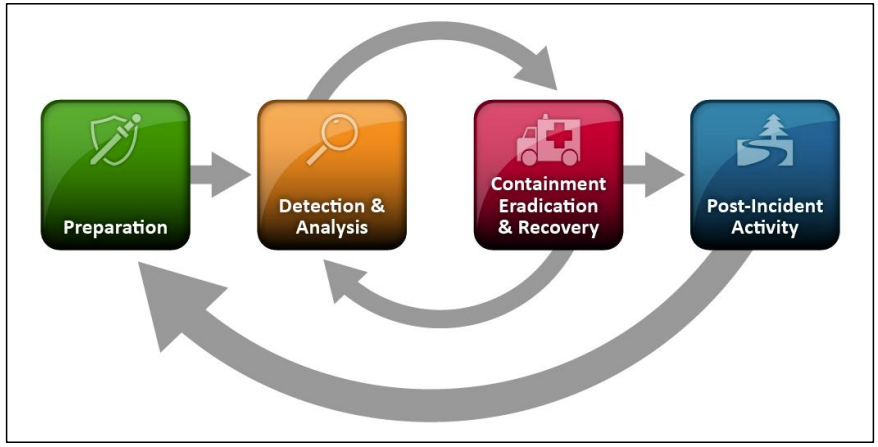
Figure 2: Incident Response
Another challenge is bringing the right people to a potential incident. Choosing the right MDR provider helps ensure the right people are always available when required. This includes scaling up as needed.
Gartner recommends the following MDR considerations.
- Use an MDR as the SOC when staffing and budget make it unreasonable to have an internal SOC.
- Use an MDR to achieve effective 24/7 incident response, including IoC/IoA detection, triage, containment, and eradication. A close working relationship between the vendor and the customer organization can also help with preparations for an incident.
- Ensure that any MDR vendor will comply with the organization’s policies during containment operations.
- Ensure that your vendor aligns well with the technology in use and its deployment environment, including the cloud.
Final Thoughts
Extended detection and response is today’s best practice for managing incidents. It provides for a complete analysis of all information resources across all locations. Using historical and current data, AI processes can detect current or past incidents and help identify the next steps.
Most organizations cannot afford the 24/7 attention required for optimum XDR deployment. MDR helps meet this challenge by engaging a vendor to manage existing and vendor-provided XDR capabilities.
MDR is not a solution that allows a customer organization to ignore its responsibility for ensuring incident management effectiveness. For example, the organization should meet monthly with the MDR provider to review how well the organization’s expectations were met. This requires setting standards of performance for the MDR vendor as part of the service agreement.





