5 Employee Types Most Likely to Steal Company Data
Given that the average cost of a data breach is nearing $5 million, you should be on the lookout for employee threats. Discover the five types of employees that are most likely to cause a data breach and the psychological drivers behind their actions.
The biggest threat to cybersecurity is probably an employee threat.
Cybersecurity Insiders’ 2024 Insider Threat report found that 71% of organizations feel at least moderately vulnerable to insider threats. Of this, 52% don’t feel they have the tools necessary to handle insider threats. It has become harder than ever to secure the network perimeter in a work-from-home (WFH) world.
Securing the network perimeter in a work-from-home (WFH) world has become more complicated. Your employees are probably using company devices for personal purposes. They might connect an unauthorized endpoint to a company-provided lease line. They might even go to the extent of conducting malicious activity for financial or personal gains.
Insider threats have become such a massive pain point that cybersecurity giant Proofpoint spent $255 million on acquiring insider threat intelligence company ObserveIT.
It is possible to preempt and prevent a significant portion of risks by monitoring employees, studying their behavior, and implementing the proper access privileges. But how do you decide which employee personas need the most attention? How can you make smarter decisions to keep insider threats to a minimum? In this article, we roundup five types of employees that have historically caused data thefts intentionally.
Learn More: Insider Threat – How to Address the ‘Human Dilemma’ in WFH Era
Five Employee Types that Could Be Placing Your Data at Risk
Did you know that the average cost of a data breach or theft in 2024 is a staggering $4.88 million? Insider threat mitigation doesn’t just keep your business operations and customer data safe – it can save you millions in penalties, litigation costs, investigation efforts, and damage to brand reputation. These five employee personas are at the root of most insider threat incidents:
Employee Threat #1: Privileged users with the highest level of access
In this scenario, the employee and the organization are equally to blame. It is a well known best practice to provide employees with least-privilege access, where data is limited to those personas who need it for their day-to-day job role.
Former Google executive and Otto co-founder Anthony Levandowski, a privileged user who worked for Google’s self-driving division was recently sentenced to 18 months in prison for trade secret theft. The engineer was accused of stealing documents that contained information related to autonomous vehicle technology before founding his own self-driving truck startup Otto.
Meanwhile, Canadian financial services provider, Desjardins Group suffered a similar fate in 2019. A Desjardins employee who stole 4.2 million data records of the financial cooperative’s members gained further access to information about 1.8 million credit-card holders. In 2019, the company warned its customers about the incident, which occurred in the latter half of 2018 but did not clarify its exact cause.
Preventing risks of this nature is as simple as implementing a strong identity access management (IAM) solution, which automatically restricts access to data, applications, and other company assets. Your security team should also regularly review access lists and privilege protocol to ensure they revoke heightened privileges where necessary.
Employee Threat # 2: Employees facing personal, financial, or professional stressors
An employee with legitimate data access may be tempted to sell the information to an illegitimate third-party due to financial stressors. This is among the most common reasons for data theft. According to the latest Verizon Data Breach Investigations Report, financial motivation tops the list, followed by espionage. Similarly, professional stressors (e.g., career frustrations, or difficulty in improving performance), as well as personal ones, can act as trigger events for data theft.
Cybersecurity giant Trend Micro had to deal with this type of insider threat in 2019. It appeared to be a small problem at first – an employee with access to customers’ home phone numbers sold them to a third-party. However, the third party then started calling up customers impersonating Trend Micro support staff. Trend Micro investigated the incident and eventually terminated the employee.
While it isn’t possible to curb all malicious attacks of this type, companies can keep a watch on employees’ financial state. Heavy debt, unusual spending habits, unprecedented medical costs, and a host of other justifiable or unjustifiable challenges might push an employee to sell data.
Employee Threat #3: Employees with prior non-compliance & misconduct history
Repeat offenders are common in corporate environments, and this shouldn’t come as a surprise. Certain employee types are prone to breaking the rules and being non-compliant, despite warnings and training sessions. Notably, an employee exhibiting negative workplace behavior could bring that same disposition to how they handle data.
Social engineering and insider threat expert, Lisa Forte, suggested that a phenomenon called cognitive dissonance might be at the root of non-compliant behavior. “We need to understand cognitive dissonance, which is when we know we’re supposed to do one thing, but we’d like to do another. So, for instance, we might know that we’re supposed to encrypt an email, but we also know that it will make our jobs faster and easier to not encrypt it, so we make excuses,” she said.
Consider Morrisons Supermarkets’ 2013 data theft incident, of which the company was acquitted from liabilities in April 2020. An employee named Andrew Skelton worked for the company’s internal audit team. After a minor misconduct, Skelton went through disciplinary proceedings and received a verbal warning. This caused a grudge, inciting Skelton to reveal Morrison’s employees’ personal data on the internet and to three British newspapers. Fortunately, the newspapers reported the incident instead of publishing the information.
Employers should watch for employees who display non-compliant behavior and ensure they have an outlet for personal and professional frustrations. Management may also want to communicate regularly with close colleagues and team members. In extreme cases, companies may terminate an employee before the situation escalates.
Learn More: How to Securely Scale Insider Threat Management Without Putting Data at Risk: CTO View
Employee Threat #4: Disgruntled employees with conflict-ridden customer relationships
Today, if a customer relationship gets soured for some reason, an employee could express their anger by stealing data.
Data theft is a real possibility for an unhappy employee with little decision-making power but access to sensitive data. An individual’s personal data is integral to their identity, their ability to do business, and fiscal wellbeing. When the data falls into the wrong hands, it can be damaging. If your organization works with high-value clients or products, this can be a particular pain point.
For instance, in 2021, a disgruntled former employee of Cash App downloaded the personal information of more than 8 million users. The employee had permissions to view the files before they left the company, but access was not turned off after employment ended. CashApp and parent company Block ended up paying $15 million in 2024 to settle a class action lawsuit for negligent behavior in response to the breach.
Companies should regularly talk to employees to understand any underlying grudges, insecurities, or unhappiness that might play out in the workplace.
Employee Threat #5: Former employees with unverified backgrounds
The time between an employee resigning and leaving the premises is a sensitive period. The employee continues to have access to privileged information but is no longer (emotionally) obligated to the employer. This is a perfect time for a dubious employee with a criminal background or a political motive to perform data theft.
Employees with dubious backgrounds can also be called “masqueraders,” as there is always an underlying risk of the employee stealing data. They are simply masquerading as a legitimate worker of the company.
In one example, former Apple employee Xiaolang Zhang stole trade secrets during his last days at the company. Zhang returned from paternity leave on 30 April 2018 and submitted his resignation soon after – expressing his intention to move back to China. Apple reviewed Zhang’s network and building access activity before his return and caught him smuggling circuit boards, a Linux server, and more from his office on April 28. In addition, it appeared that Zhang was unusually active on leave, weeks before he would submit his resignation. Apple contacted the FBI, which filed a criminal complaint against Zhang. Zhang was sentenced to six months in prison and fined nearly $150,000.
Potential Risk Indicators for Employee Threats
Monitoring employee activity can alert companies to red flags long before a data theft can take place. It is vital to conduct detailed exit interviews, best practices adherence checks, and even background checks for employees working with high-value intellectual property.
The Center for Development of Security Excellence (CDSE), trains leaders in the US Department of Defense security community and hosts the annual National Insider Threat Awareness Month each September. It maintains that insider threats are most vulnerable when there isa combination of opportunity and crisis in their environment. Most insider threats exhibit one or more potential risk indicators, including predispositions, life stressors, bad behavior, and problematic performance.
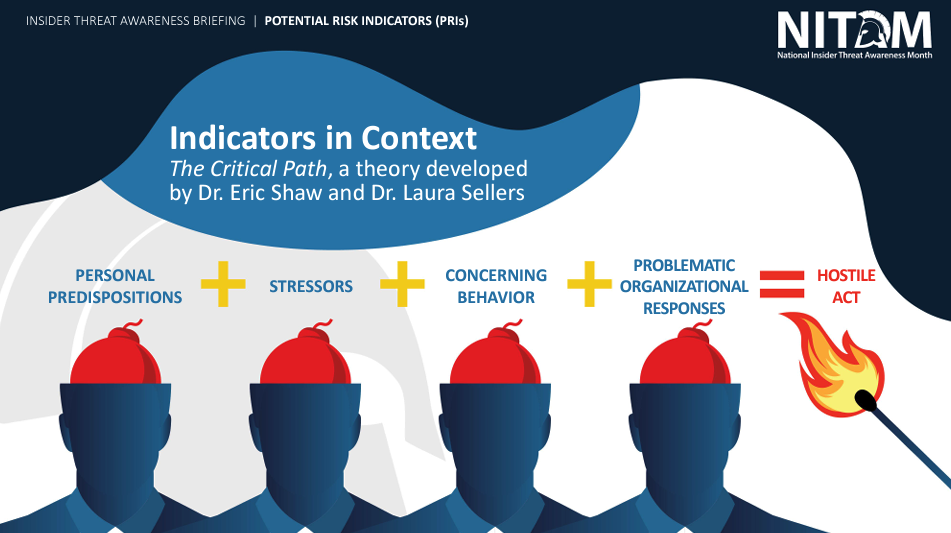
Source: National Insider Threat Awareness Month (NITAM) Threat Awareness Briefing
Research by Kim, Oh, Ryu, Lee, Kwon, and Lee segment data thieves and insider threats into three categories, including masqueraders. They deliberately escalate the level of privilege at a company so that they can perfectly time the breach.
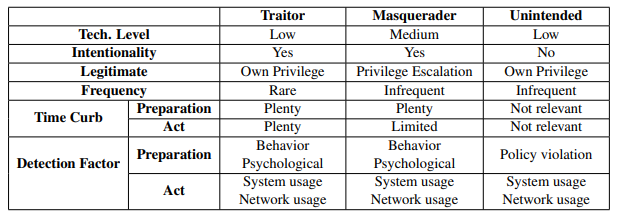
Source: A Systematic Review of Insider Threat Detection
Preempting and Mitigating Employee Data Theft
Instances like these make it evident that in a world of high-stakes cybercrime and data theft challenges, employee threats need to be taken seriously. Organizations need to start with implementing appropriate identity and access management protections. But you shouldn’t end there. Technology can rarely correct a people problem. You’ll also need to implement security awareness training. Another suggestion is to ensure that your employees are engaged with their work, the company, and their colleagues. Instilling a sense of loyalty can go a long way to warding off any employee threats.
A good example of this is when a Russian citizen offered a Tesla employee $1 million to install malware on the company network. The Nevada factory employee contacted the FBI and went undercover to bring the culprit to justice. That’s the kind of insider you want on your team.






