November 2024 Patch Tuesday – 89 Microsoft CVEs Addressed
Microsoft rolled out fixes for 89 new vulnerabilities, 4 of which have been categorized as zero-day. 4 are rated critical, 83 are important, and one is moderate.

Microsoft releases a monthly security update on the second Tuesday of each month. In November’s update, the company addressed and released fixes for 89 Microsoft CVEs and republished 3 non-Microsoft CVEs. Four zero-day vulnerabilities were addressed, including two that are actively being exploited.
The November Patch Tuesday release is about 25% smaller than last month’s update, which identified 117 vulnerabilities. This time, most vulnerabilities fell in the remote code execution (59%) or the elevation of privilege (30%) categories.
November 2024 Patch Tuesday Zero-Day Vulnerabilities
Actively Exploited
- CVE-2024-43451 is a spoofing vulnerability in the New Technology LAN Manager v2 protocol which could allow an attacker to see a user’s hashed password. The attacker could then use this to access the system as that user. It ranks medium in severity with a CVSS score of 6.5.
- CVE-2024-49039 is an elevation of privilege vulnerability in Windows Task Scheduler. The attacker could infiltrate a low privilege AppContainer and elevate their privileges. This may allow them to execute tasks that are restricted to privileged accounts. It ranks high in severity with a CVSS score of 8.8.
Publicly Disclosed
- CVE-2024-49040 is a spoofing vulnerability in Microsoft Exchange Server that could allow attackers to successfully send a message as a forged sender as if it were legitimate. It ranks high in severity with a CVSS score of 7.5.
- CVE-2024-49019 is an elevation of privilege vulnerability in Active Directory Certificate Services which could allow an attacker to obtain domain administrator privileges due to weak authentication. The vulnerability ranks high in severity with a CVSS score of 7.8.
November 2024 Patch Tuesday Critical Vulnerabilities
While the November update has 83 issues ranked important, only 4 critical ones exist.
.NET and Visual Studio
CVE-2024-43498
Exploit: A type confusion weakness could allow an attacker to send specially crafted requests to a .NET web application or desktop application to execute remote code.
Windows VMSwitch
CVE-2024-43625
Exploit: An attacker could trigger a “use after free” vulnerability in a virtual machine’s Hyper-V host to obtain host privileges. a Hyper-V guest with low privileges could traverse the guest’s security boundary and launch a successful attack.
Windows Kerberos
CVE-2024-43639
Exploit: An unauthenticated user could create a custom program to exploit a weakness in the Windows Kerberos security system, allowing remote code execution on the targeted computer.
airlift.microsoft.com
CVE-2024-49056
Exploit: Unauthorized users could elevate privileges via authentication bypass because data is assumed to be immutable. Microsoft has already mitigated this vulnerability.
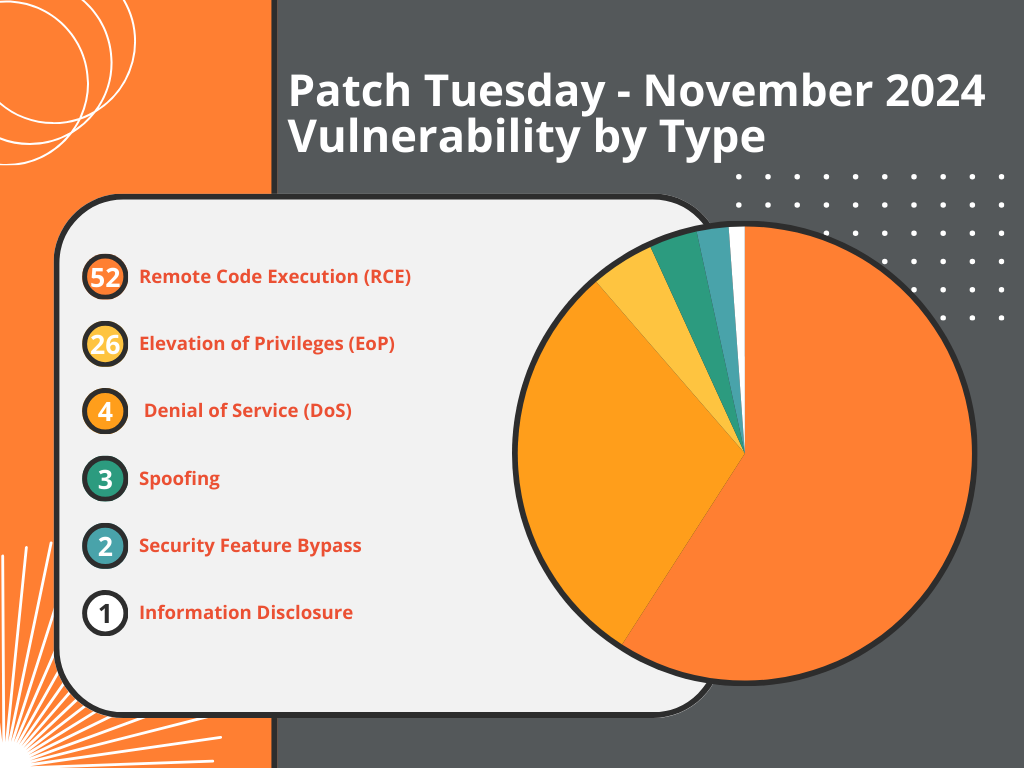
November 2024 Patch Tuesday Breakdown
The vulnerability categorization for November 2024 is as follows:
- 52 Remote Code Execution (RCE)
- 26 Elevation of Privileges (EoP)
- 4 Denial of Service (DoS)
- 3 Spoofing
- 2 Security Feature Bypass (SFB)
- 1 Information Disclosure
Microsoft’s Security Response Center has a complete list of vulnerabilities, including the CVE number, base CVSS score and vectors, potential for exploitability, and more.






